

21% of components in most popular open-source projects harbor backdoor vulnerabilities that enable direct network access. These vulnerabilities are more easily exploitable.

Can you detect pre-tampered components like XZ in your applications?

Open-source developers are great innovators. Great maintainers? Not so much!

Lineaje analysis on a sample of set of 59 project from the Top 150 "Most Critical" open-source projects as designated by Linux OpenSSF .


You hire contractors to do a job. Your contractors hire sub-contractors. The sub-contractors hire more sub-contractors creating a chain that may be 30 levels deep. And soon, you no longer know theorigin of some people working on your job. How risky is that?


There is a spectrum from fully known to completely unknown components. Do you know that distribution for your software application?

OSS hides 2/3rd of its inherent risks and your existing tools cannot detect them.

In the ever-evolving landscape of software development, Open-Source has become a cornerstone for innovation and efficiency. However, our recent analysis has shed light on a crucial aspect that demands our attention – the inherent risks associated with Open-Source components. In our comprehensive study, we discovered that a shocking 82% of components in Open-Source software carry inherent risks. This finding not only underscores the prevalence of challenges but also emphasizes the need for a strategic approach to mitigate potential risks and vulnerabilities.
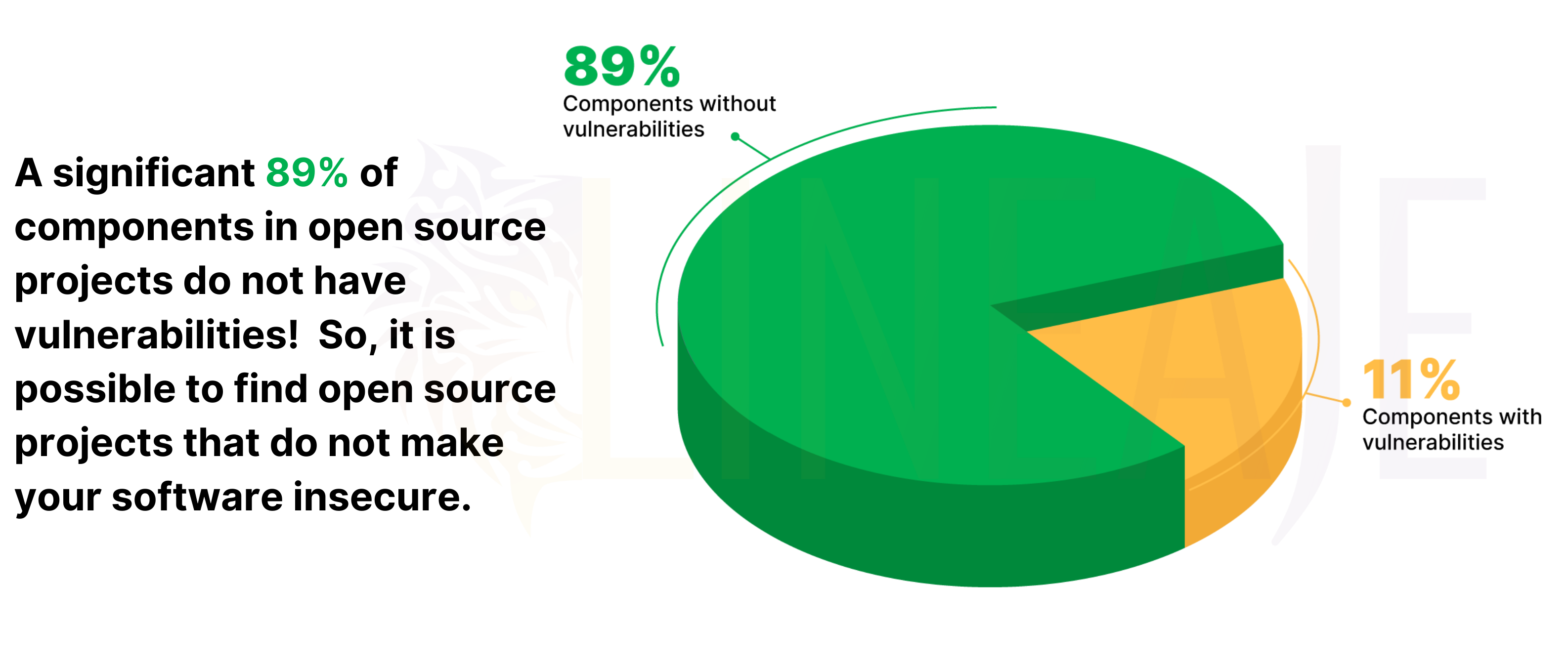
Recent findings based on Lineaje Labs study, reveal that a significant 89% of components in open source projects are free from vulnerabilities! This discovery challenges the misconception that open source inherently compromises software security.

The recent finding that 90% of software components in open-source software reside in transitive, invisible dependencies carries significant security implications for the software development community.

Brace yourselves for a game-changing revelation! Recent research has shed light on a pivotal security insight: a staggering 68% of code in Open Source Software (OSS) packages is contributed by providers and suppliers other than the package owner!
This finding carries profound security implications, underlining the intricate web of dependencies within OSS projects. It reinforces the critical need for a robust Software Supply Chain Security Management Service. Understanding and addressing these implications is paramount.

In today's rapidly evolving tech landscape, open-source software has become the backbone of countless applications and systems. However, a recent study by Lineaje AI Labs has shed light on a concerning statistic - a staggering 40% of open-source software components have a Critical inherent risk score.

Within open-source software, a fascinating trend has emerged: packages are reused an average of 2.7 times within the same open-source project. This phenomenon carries significant implications for security, software supply chain security, and maintenance practices within the open-source ecosystem.

Based on Lineaje AI Labs research the majority of vulnerabilities in open-source are not fixed by open source developers. Lineaje AI labs analyzed 121,443 open-source projects and discovered 118,573 vulnerabilities in them. The saving grace is that vulnerabilities are not evenly distributed across dependencies.

Based on Lineaje Labs research a staggering 77% of vulnerabilities in open-source reside within transitive dependencies (which your developers cannot patch). Open Source Projects pull in 20+ levels of dependencies. Along with those dependencies come their vulnerabilities. Lineaje AI labs analyzed 121,443 open source projects and discovered 118,573 vulnerabilities in them.

Lineaje research indicates that 8.3% of Open Source Software is of unknown origin.






Lineaje is continuously adding support for your favorite languages and integrations to connect with tools, pipelines, and workflows.



























